Secure Tap Transactions

Essential Features of NFC Payments
Near Field Communication (NFC) technology powers modern contactless payment systems, offering convenience and speed for everyday transactions. Central to its operation is the ability to establish a wireless communication link between devices, such as smartphones and payment terminals, within a very short range, typically less than 4 cm. This proximity requirement enhances security, reducing the risk of unauthorized interception of data. NFC payments support encryption and dynamic authentication processes, ensuring that each transaction is not only quick but also secure. Moreover, NFC is highly versatile, supporting a wide range of uses beyond payments, including ticketing and data sharing, making it an integral part of the digital wallet ecosystem.
The Mechanics of NFC Transactions
NFC transactions are facilitated by electromagnetic induction between two loop antennas located within each other's near field. This setup enables one device to act as a reader and the other as a tag, typically involving a payment terminal and a mobile device. The process begins when an NFC-enabled device is brought close to a payment terminal, automatically initiating communication without the need for manual pairing. Data is exchanged via NFC protocols, which are designed to complete the transaction in less than a second, ensuring efficiency. Furthermore, this technology is not limited to payments; it can also trigger digital actions like opening apps or connecting to wireless services, making NFC a versatile tool in the digital age.
Security Protocols in NFC Payments
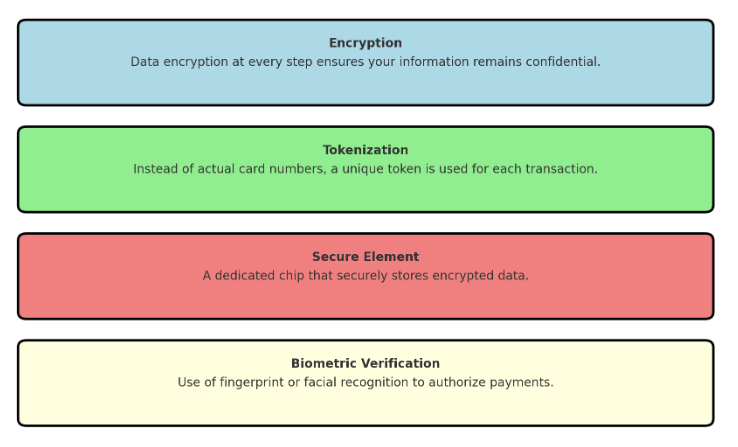
NFC payments are secured through a combination of encryption, secure channels, and tokenization. Each transaction involves encrypted data that only the sending and receiving device can interpret. This is facilitated by the secure element (SE), a tamper-resistant platform within the device that handles encryption and data storage securely. Tokenization further enhances security by replacing sensitive card details with a unique identifier, a token, which is used only for a single transaction. These tokens are useless if intercepted, as they do not carry the actual card number. Additionally, NFC payments often require authentication methods such as PINs or biometrics, adding another layer of security to prevent unauthorized use.
Vulnerabilities in NFC Systems
Despite its robust security features, NFC technology is not immune to vulnerabilities. One significant risk arises from the short-range requirement, which can be exploited through relay attacks where an unauthorized device intercepts and transmits communication between two legitimate devices over a greater distance. Additionally, eavesdropping is possible if an attacker can get a rogue device close enough to intercept the NFC signal. There is also the risk of data manipulation, where the transmitted data can be altered or corrupted. Finally, lost or stolen NFC-enabled devices could be used for fraudulent transactions if not adequately protected by additional security measures like biometrics or PINs. These vulnerabilities necessitate continual advancements in NFC security protocols to safeguard user data effectively.
Typical NFC Security Threats
NFC security threats primarily include skimming, where attackers use unauthorized devices to capture data from NFC transactions. Another common threat is the modification of NFC tags, which involves altering the data stored on NFC chips typically found in advertisements and public posters, potentially redirecting users to malicious sites. Additionally, replay attacks are a concern, where data from a legitimate NFC transaction is recorded and replayed to make unauthorized purchases. Addressing these threats requires ongoing vigilance and updates to NFC and mobile device security protocols.
Strengthening NFC Security Measures
To enhance NFC security, stakeholders are focusing on multi-layered security strategies. Key measures include the integration of advanced encryption standards to protect data transmitted between devices and the implementation of secure elements that store sensitive information in a protected environment on the device. Emphasis is also on improving tokenization techniques which ensure that transaction details are masked with a unique token, rendering the data useless if intercepted. Additionally, continuous software updates are crucial to address vulnerabilities as they arise and prevent exploits. Companies are also adopting biometric authentication, such as fingerprint and facial recognition, to secure access to NFC-enabled devices, significantly reducing the risk of unauthorized transactions. These combined efforts aim to fortify the security framework surrounding NFC technologies, safeguarding them against evolving threats.
Best Practices for Small Businesses
Small businesses can enhance NFC security by adopting a few key practices. Firstly, choosing NFC payment providers that offer robust security features, such as end-to-end encryption and tokenization, is crucial. Regularly updating software and hardware components of NFC-enabled devices ensures that security measures are current and effective against new threats. Educating employees about security protocols and potential fraud tactics can also prevent unauthorized access and misuse. Additionally, implementing strong customer verification methods, such as requiring PINs or biometric data for transactions, adds an extra layer of security, safeguarding both the business and its customers from financial loss.
Choosing a Secure Card Terminal Provider
When selecting a card terminal provider, small businesses should prioritize security features to protect against NFC fraud. It is crucial to choose providers that comply with the latest Payment Card Industry Data Security Standard (PCI DSS) requirements. Look for providers offering terminals with point-to-point encryption (P2PE), which secures data from the point of entry to the processing stage. Additionally, evaluate the provider's reputation for software updates and customer support. Providers that regularly update their systems to patch vulnerabilities and offer robust fraud detection services can better safeguard your transactions and customer data.
Building Consumer Confidence with NFC Security
Consumer confidence in NFC payments can be significantly bolstered by transparent communication about the security measures in place. Businesses should actively inform customers about the encryption and tokenization processes that protect their transaction data. Demonstrating compliance with international security standards like PCI DSS can also reassure users. Additionally, providing clear instructions on what consumers can do if they suspect a security breach — such as how to report unauthorized transactions and disable NFC features quickly — enhances trust. Engaging with customers through security-focused marketing and educational campaigns can further deepen their understanding and comfort with using NFC technology safely. This proactive approach not only secures transactions but also strengthens the overall customer relationship with the technology.
Impact of Security on Customer Trust
Effective security measures in NFC payments significantly influence customer trust. When businesses implement stringent security protocols, such as advanced encryption and real-time monitoring, customers feel more secure in using NFC technologies for transactions. This trust is further enhanced when businesses are transparent about their security practices and provide clear, accessible customer support for security-related issues. Additionally, when customers experience consistent, fraud-free transactions, their confidence grows, leading to increased usage and loyalty. Ultimately, a strong security foundation not only protects the financial data but also strengthens the relationship between businesses and their customers, encouraging continued engagement with NFC payment systems.
Future of NFC Security Technologies
The future of NFC security is poised to evolve with advancements in encryption, biometrics, and artificial intelligence. Enhanced encryption techniques will continue to improve the security of data transmissions, making NFC payments even more resilient against hacking attempts. The integration of biometrics for authentication, such as facial recognition and fingerprint sensors, is expected to add a personalized layer of security that is difficult to replicate. Additionally, artificial intelligence is set to play a crucial role in real-time threat detection and response, adapting to new fraud tactics as they emerge. These technological developments will not only secure transactions but also streamline user experiences, ensuring NFC remains at the forefront of contactless payment technology. These innovations are crucial for maintaining consumer trust and expanding the use of NFC in various sectors.
Emerging Trends in Biometric and AI Security
Biometric and artificial intelligence (AI) technologies are rapidly transforming NFC security. Innovations in biometric security now include more sophisticated facial recognition systems and advanced fingerprint sensors that provide a higher level of accuracy and fraud resistance. AI is enhancing security by learning from transaction data to identify and respond to fraudulent patterns in real-time. These technologies not only make NFC transactions more secure but also improve the speed and user-friendliness of authentication processes. As these technologies continue to develop, they promise to significantly enhance the security landscape for NFC and other digital payment methods.
We at NFC Tagify provide all sort of NFC Solutions or you may contact us: Tel. 01600800080, Email: info@nfctagify.com








